Overriding a Cross-Account IAM Role
A cross-account authorized by an IAM-based-role has the disadvantage of being used by many users. All users of that account use the same role and are granted the same Amazon S3 permissions. This scenario may not be suitable in a large enterprise. To overcome this issue, Qubole provides a feature to override the cross-account’s IAM role settings at the user-level in an account.
Overriding an IAM role requires performing the following three steps related to IAM policies :
Qubole-generated External ID can avoid the misuse of the Role-ARN from assuming IAM role-based authorization by multiple users.
Obtaining the External ID
Note
An optional, but recommended step to avoid the misuse of the Role-ARN from assuming IAM role-based authorization by multiple users.
The following figure illustrates a default IAM-role-based account that contains the clone and overriding options in the drop-down list.
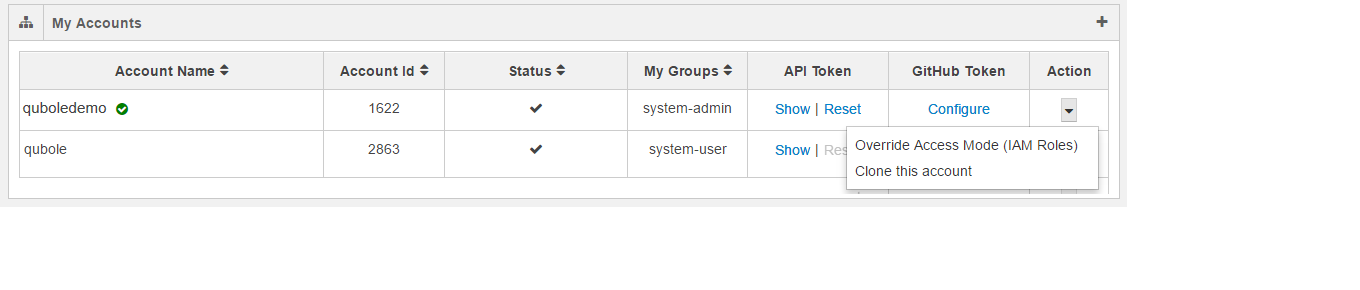
Click Override Access Mode (IAM Roles) and the dialog to override the IAM roles account. The dialog shows a text field to enter Role ARN and a check box to enable External ID. Qubole-generated External ID can avoid the misuse of the Role-ARN from assuming IAM role-based authorization by multiple users. If you select the check box to enable External ID, the external ID is displayed as shown in the following figure.
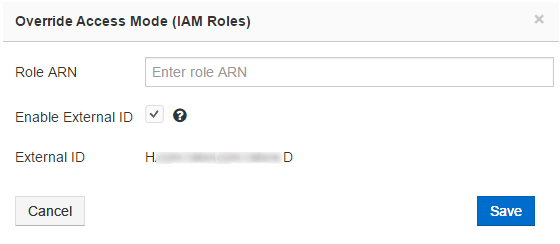
Click Save after entering the Role ARN to override the account-level IAM role settings. Click Cancel to revert to the previous My Accounts tab.
For more information on:
How to override the IAM-Role-based account, see Overriding an IAM-Role-based Account (AWS).
Users and accounts, see Users and Accounts.
Creating a User-level Role Amazon S3 Policy
Perform the following steps to create an Amazon S3 Policy:
Navigate to the Identity and Access Management interface.
Navigate to the Policies interface within the Identity and Access Management interface.
Click Create Policy.
Click Create Your Own Policy.
Enter a Policy Name for the Amazon S3 policy.
Provide a Policy Description.
For the Policy Document, use the following code and update the text as required.
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": [
"s3:DeleteObject",
"s3:GetObject",
"s3:GetObjectAcl",
"s3:PutObject",
"s3:PutObjectAcl",
"s3:GetBucketAcl",
"s3:GetBucketLocation",
"s3:ListBucket"
],
"Resource": [
"arn:aws:s3:::<user-bucketpath/*>",
"arn:aws:s3:::<user-bucketpath>",
"arn:aws:s3:::<default-location>",
"arn:aws:s3:::<default-location/*>"
]
},
{
"Effect": "Allow",
"Action": [
"s3:GetObject",
"s3:ListBucket"
],
"Resource": [
"arn:aws:s3:::paid-qubole/*",
"arn:aws:s3:::paid-qubole"
]
}
]
}
Note
In the above policy example, replace the <user-bucketpath>.
Click Create Policy.
Note
The asterisk (*) after the slash (/) in the first line under Resource indicates all sub directories stored in the location provided to the left of the slash (/).
The Amazon EC2 policy of the cross-account IAM Role is used for overridden roles created from that account.
Updating a User-level Role Trust Policy
Perform the following steps to update trust relationships of the newly create AWS IAM service role:
Navigate to the Identity and Access Management interface.
Navigate to the Roles interface within the Identity and Access Management interface.
Click the new cross-account IAM role.
Click the Trust Relationships tab.
Click Edit Trust Relationships.
For the Policy Document, use the following code and update the text as required.
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Principal": {
"AWS": "arn:aws:iam::<customerawsaccountid>:role/<cross-account-role>"
},
"Action": "sts:AssumeRole",
"Condition": {
"StringEquals": {
"sts:ExternalId": "<externalid>"
}
}
}
]
}
Note
In the above policy example, replace the customerawsaccountid and externalid.
After editing, click Update Trust Policy to save changes.
Return to Qubole UI. Enter the Role ARN and option of
externalidunder my accounts section. For more information, see Managing Roles. See Overriding an IAM-Role-based Account (AWS) for more information on override Role ARN.
Supported Commands by an Overridden IAM Role
The following commands are supported by an overridden IAM role:
Shell command
Hive command
Hadoop command
Spark command except DDL commands
Pig
Presto. The support for Presto command is not enabled by default. To enable it, create a ticket with Qubole Support.
Limitations of an Overridden IAM Role
The My Amazon S3 option in the Explore page and S3 dependency in a Qubole Scheduler do not work in a user-level IAM Role.